Mullvad VPN for Windows
Latest version: 2025.7 (see changes)
Works on Windows 10 or later (64 bit only)
Psst! Beta versions are also available in the Mullvad VPN loader, download it from the “Download” button above.
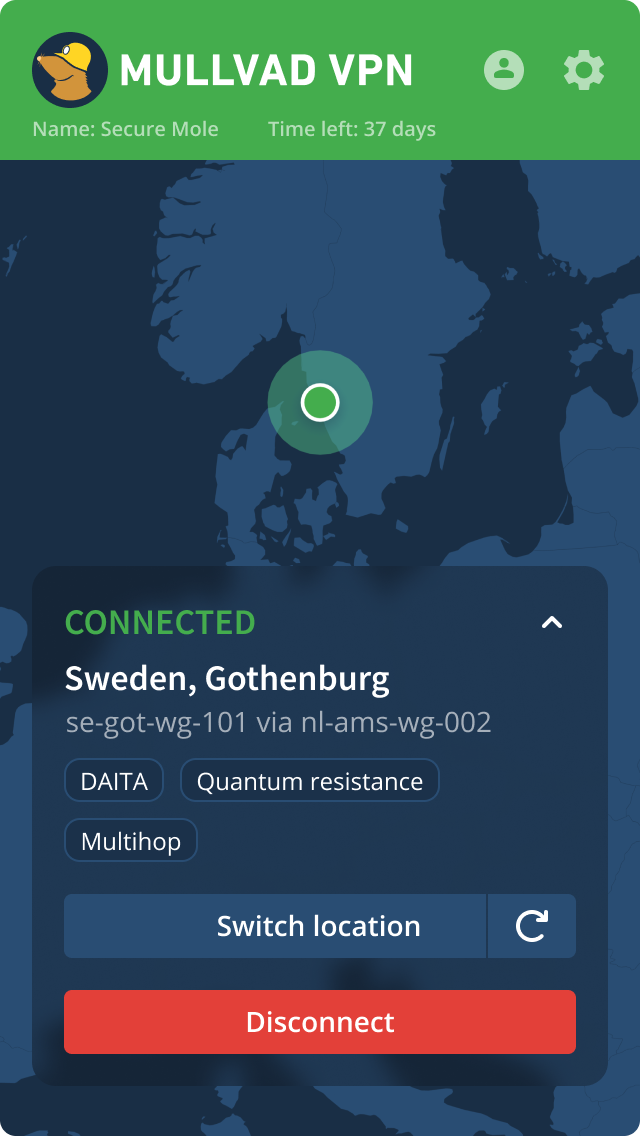
Ease of use
- Install and get a tunnel running in a few clicks
- Change location/server easily
- Submit support requests directly in the app
- Split tunneling
Securing your privacy
- Automatic WireGuard key rotation, anti censorship, port probing and traffic obfuscation
- Advanced kill switch. Tight firewall integration with atomic operations without leaks
- Multihop and Shadowsocks
- Cryptographically signed installer
- We have a no-logging of user activity policy
Trust is paramount
- Latest App audit (November 2024 – by X41 D-Sec)
- Our source code
Alternative installation
If the default installation method doesn't work, you can download the standalone installer instead.