DAITA: Defense Against AI-guided Traffic Analysis
Even if you have encrypted your traffic with a VPN, advanced traffic analysis is a growing threat against your privacy. Therefore, we have developed DAITA – a feature available in our VPN app. Through constant packet sizes, random background traffic and data pattern distortion, we are taking the battle against AI-guided traffic analysis.
When you connect to the internet through a VPN (or other encrypted services, like the Tor Network for instance) your IP address is masked, and your traffic is encrypted and hidden from your internet service provider. If you also use a privacy-focused web browser, you make it harder for adversaries to monitor your activity through other tracking technologies such as third-party cookies, pixels and browser fingerprints.
But still, the mass surveillance of today is more sophisticated than ever, and a growing threat against privacy is the analysis of patterns in encrypted communication through advanced traffic analysis.
This is how AI can be used to analyze your traffic – even if it’s encrypted.
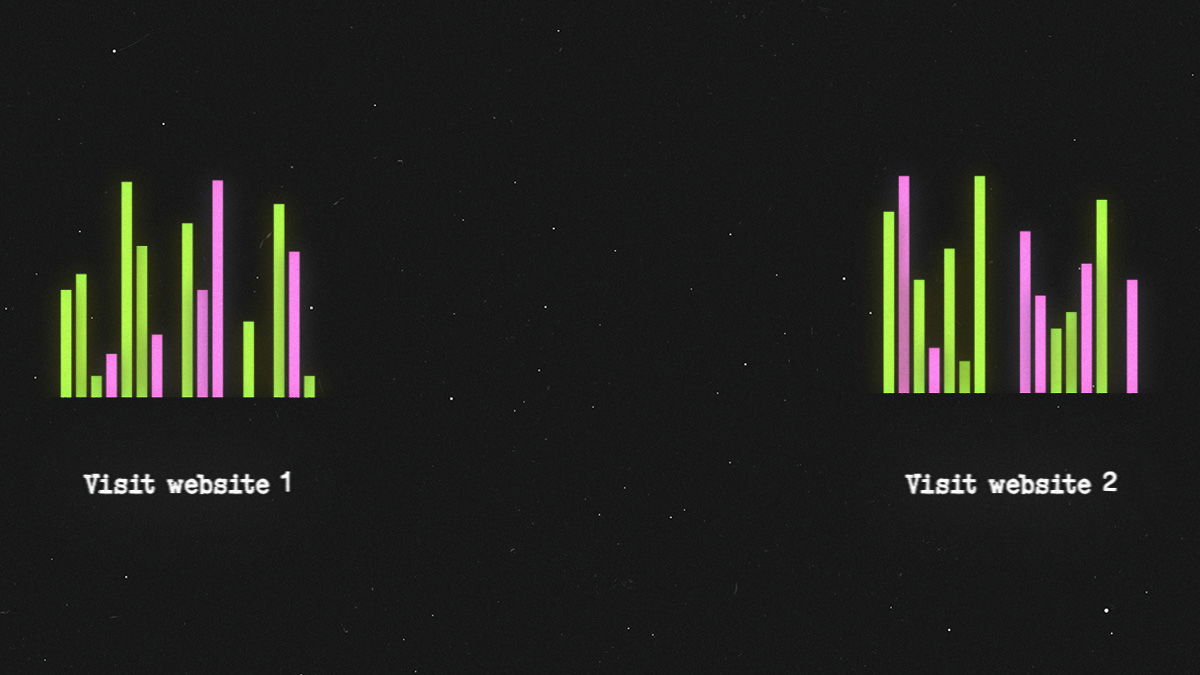
When you visit a website, there is an exchange of packets: your device
will send network packets to the site you’re visiting and the site will
send packets back to you. This is a part of the very backbone of the internet.
When you use encrypted services like a VPN the content of these packets
(which website you want to visit for example) is hidden from your
internet service provider (ISP), but the fact that these packets are being
sent, the size of the packets, and how often they are sent will still be
visible for your ISP.
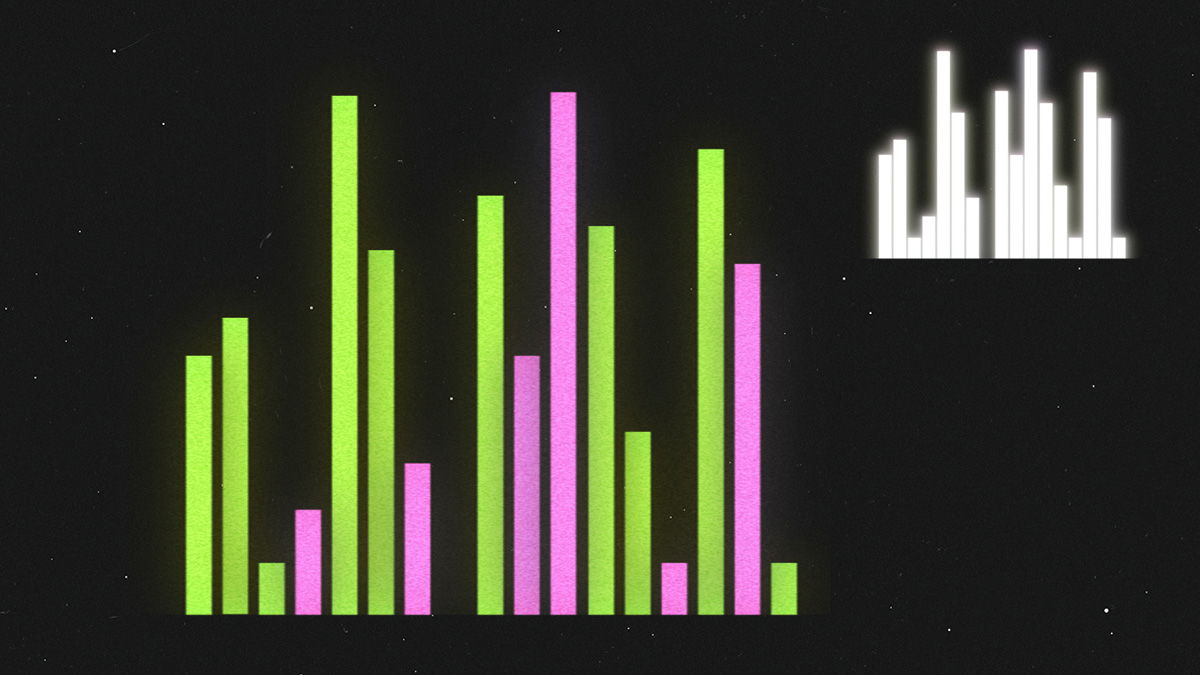
Since every website generates a pattern of network packets being sent back and forth based on the composition of its elements (like images, videos, text blocks etcetera), it’s possible to use AI to connect traffic patterns to specific websites. This means your ISP or any observer (like authorities or data brokers) having access to your ISP can monitor all the data packets going in and out of your device and make this kind of analysis to attempt to track the sites you visit, but also identify whom you communicate with using correlation attacks (you sending messages with certain patterns at certain times, to another device receiving messages with a certain pattern at same times).
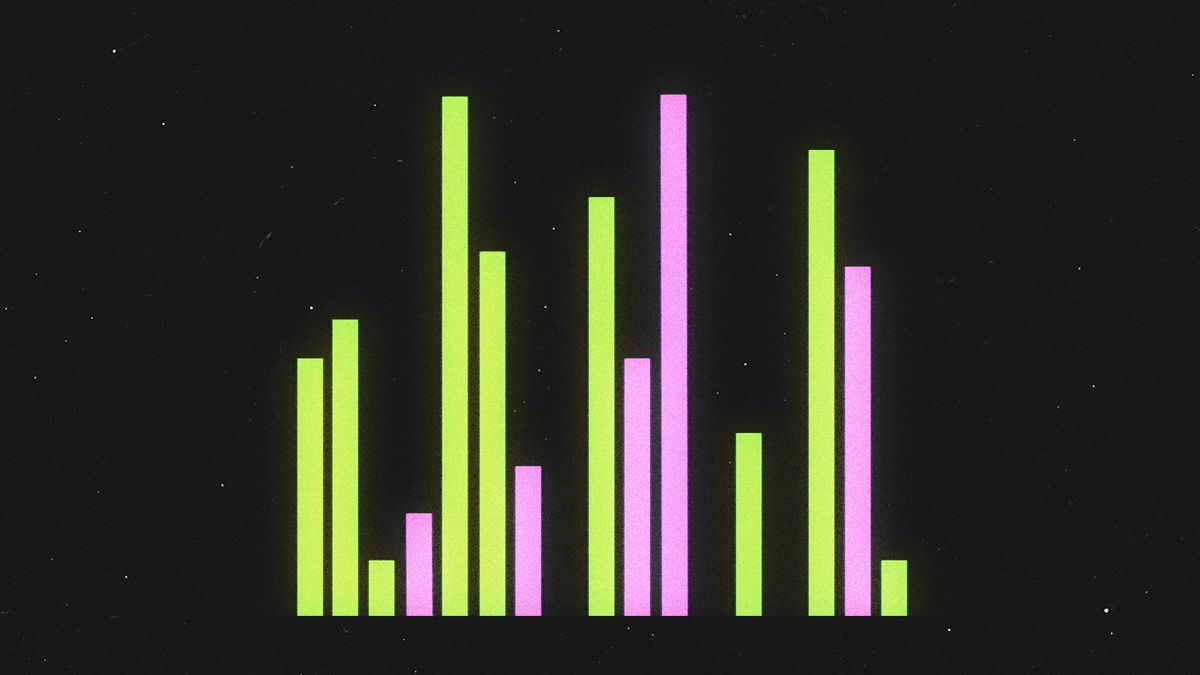
Green: packets sent from your device to the website.
Pink: packets sent from the website to your device.
How we combat traffic analysis: this is how DAITA works.
DAITA has been developed together with Computer Science at Karlstad University and uses three types of cover traffic to resist traffic analysis.
1. Random background traffic
By unpredictably interspersing dummy packets into the traffic, DAITA masks the routine signals to and from your device. This makes it harder for observers to distinguish between meaningful activity and background noise, making it hard to know if you are active or not.
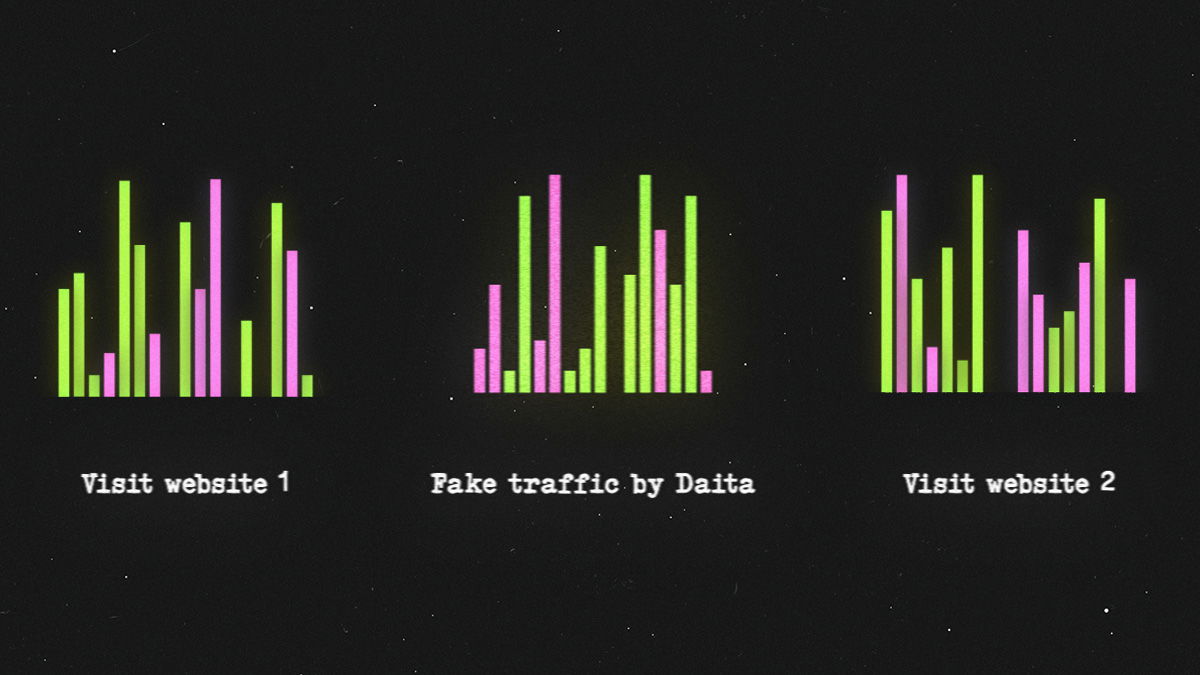
2. Data pattern distortion
When visiting websites (or doing any other activity that causes significant traffic), DAITA modifies the traffic pattern by unpredictably sending cover traffic in both directions between client and VPN server. These “fake packets” distorts the recognizable pattern of a website visit, resisting accurate identification of the site.
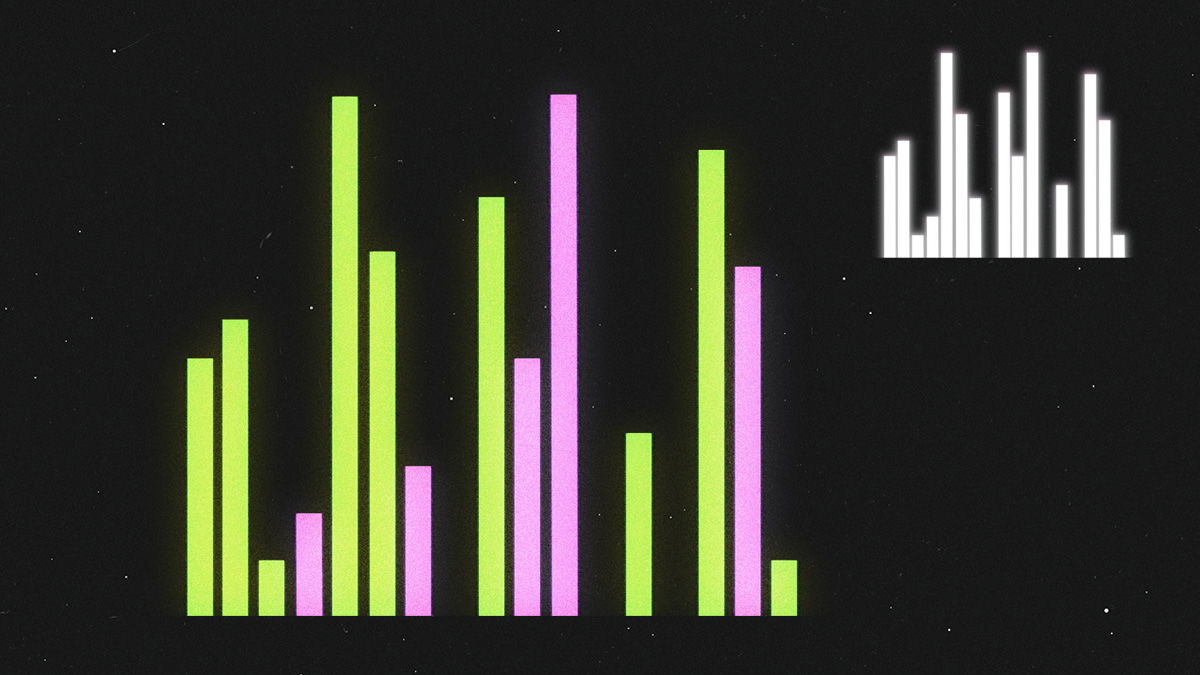
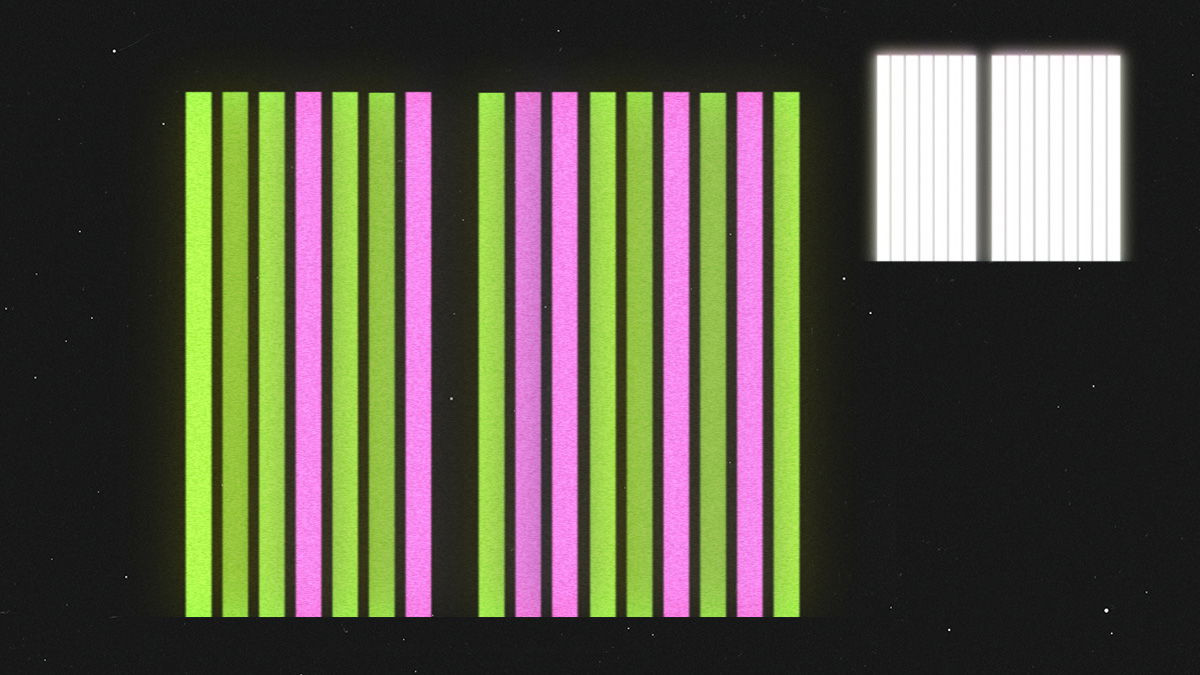
3. Constant packet sizes
The size of network packets can be particularly revealing, especially small packets, so DAITA makes all packets sent over the VPN the same constant size.

The building blocks of DAITA are open source
DAITA is built using the open-source Maybenot defense framework, which Mullvad helps to fund development of. The work has been academically peer reviewed and published as open access.
DAITA is available in our VPN apps (supported on all platforms).
Note: For now, DAITA is only available on select servers in Amsterdam, London, Los Angeles and New York. More information about this in your app.