Adding another layer: Malware DNS blocking
DNS blocking has become a well received addition to our service, particularly via our app. Today we announce an expansion of this service with malware blocking.
Last year we announced a new feature for blocking advertising and trackers system wide via our apps. These were based on lists that are readily available and viewable via our Github page.
Now available everywhere: Blocking websites serving malware
This service is an extension to our other blocking services, where we block lists of known websites that serve malicious content. This feature can be used alongside our advertising and tracker blocking features, and can be enabled either via a toggle available in our desktop and iOS apps or via a custom DNS entry if you are on Android, or are using our service via a configuration file.
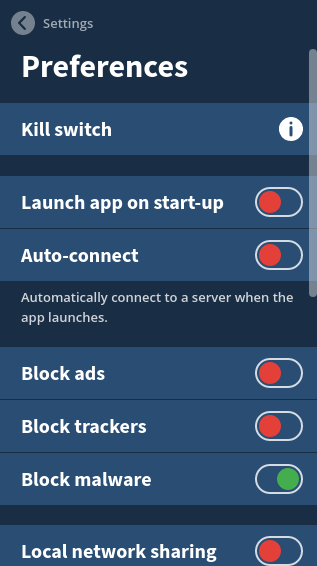
To use this feature
For desktop and iOS:
- Select the Cog → Preferences → Block malware
For Android:
- Select the Cog → Advanced → Use custom DNS and enter one of the following IP addresses that matches your desired state.
For Android and configuration file users you will need to use one of the following custom DNS entries to enable this feature:
- 100.64.0.4 - Malware blocking only
- 100.64.0.5 - Ad and malware blocking, no tracker blocking
- 100.64.0.6 - Tracker and malware blocking, no ad blocking
- 100.64.0.7 - Ad, tracker and malware blocking (“everything”)
Malware blocking was made available with the app release 2022.1 on desktop and iOS.
We will add this toggleable feature to Android as well in a future release.
Behind the scenes (for the nerds only)
For malware URL blocking we make use of URLHaus' RPZ list which we import into our OpenVPN and WireGuard servers. Since this list is frequently updated from URLHaus, we want to ensure that our lists are refreshed to match in a similar cadence.
These lists are included in a new Bind zonefile that sits alongside our other blocking zonefiles. Whereas the other lists are imported from our Github repository, the malware list we use currently is taken directly from URLHaus.
Each Bind view is then assigned an IP address which is used to specify which list, or combination of lists should be used.
The following list demonstrates the IP address to list combinations:
If you want to use custom DNS via our app, you can use the corresponding IP address from this list.
- 100.64.0.1 - Ad blocking only
- 100.64.0.2 - Trackers only
- 100.64.0.3 - Ad blocking, trackers, no malware blocking
- 100.64.0.4 - Malware blocking only
- 100.64.0.5 - Ad blocking, malware blocking, no tracker blocking
- 100.64.0.6 - Tracker, malware blocking, no ad blocking
- 100.64.0.7 - Ad blocking, tracker and malware blocking (“everything”)
We now deem our DNS-adblock repository to be stable, and have been investigating more lists that we can add to it. Previously we were refreshing the lists we had on a monthly basis.
This is not intended to be a replacement for good security practices, nor is it meant to be a replacement for an anti-malware tool. Please ensure you use this in conjunction with other practices to keep your computers and mobile devices safe, secure and up to date.
This initial deployment is bare bones, and will be updated in the future once we verify its stability and potentially get our customers feedback. If you have any thoughts regarding the malware list that we utilise please contact our Support Team by email: support@mullvad.net
"WireGuard" is a registered trademark of Jason A. Donenfeld.