The limitations of split tunneling
You’ve made it to the halfway point of our split tunneling series! In Part 3, get a little technical as we inspect some limitations of our split tunneling implementation and how to work around them.
Let’s dive right into the limitations that our split tunneling solution presents. We’ll also mention how to work around them.
Name resolution
Due to how DNS is configured and used on most platforms, requests will still be sent inside the tunnel, even for applications that are selected to have their traffic excluded.
Let’s use the gaming scenario to see how this could cause issues
Imagine that you are located in Japan and connected to a VPN server in California. But to achieve low round-trip times when playing your favorite online game, you use split tunneling to exclude your gaming traffic from traveling across the ocean and back.
As with many online games, the one you play has its servers scattered around the world. It also uses DNS to assign servers to its players. Because of this, it will pick the server closest to your VPN location, in this case California.
So even though your gaming traffic is traveling outside of the VPN tunnel (thanks to split tunneling), it's being sent to a server far, far away. This means you won't experience the performance boost that split tunneling can provide.
Two ways in which this can be mitigated
- Enable DoH/DoT (DNS over HTTPS/DNS over TLS) in the game client to override DNS hijacking on the VPN server. DNS traffic will then be sent, encrypted, between yourself and your configured DNS server. You can try our DoH/DoT service, but if none of our DNS servers are near you, then nothing will be gained.
- Connect to a VPN server in your area. In this case, the game server will still be selected based on the VPN server’s location. But since you and the server are in the same region, the end result should be the same, as a game server close to both of you will be selected.
Competing network software (in Windows)
It could happen that split tunneling stops working if you have multiple applications (kernel drivers) that are fighting to manage new network connections. You'll experience this as split apps being offline.
Examples of software that could collide with the split tunneling functionality include proxy software, firewalls, and similar security software. Sometimes the collision is caused by using overlapping configurations, other times, merely having the applications installed simultaneously could result in collisions.
If split tunneling stops working in this manner, it's only the splitting logic that becomes ineffective. Security is guaranteed and anti-leak protection remains intact. In other words, all traffic that can’t be split and is heading for the tunnel is safely blocked. This is in full contrast to other split tunneling implementations we have examined.
This issue can only be resolved by modifying the set of installed apps or their internal configurations.
Localhost communications (in Windows)
This issue is only present in the Windows implementation of split tunneling, thanks to somewhat a perfect storm.
There's an issue with client software attempting to connect to localhost. Excluded apps are generally prevented from connecting to local services on a UDP socket. This can be a problem if an excluded app needs to communicate with a daemon on the local machine and uses network sockets for this communication. An example would be if an excluded app tries to use a proxy service running on the local machine.
There's no general workaround for this issue. You'll need to change your configuration on a case-by-case basis.
Connection lifetimes (in Linux)
This issue is only present in our implementation of split tunneling on Linux.
Most connections that are established from excluded apps are dependent on the lifetime of the VPN tunnel. An exception to this is any local connection that has the destination address on the local network, in other words, connections to devices on your LAN.
Therefore, anytime you switch VPN servers or explicitly disconnect the VPN tunnel, affected connections will be broken.
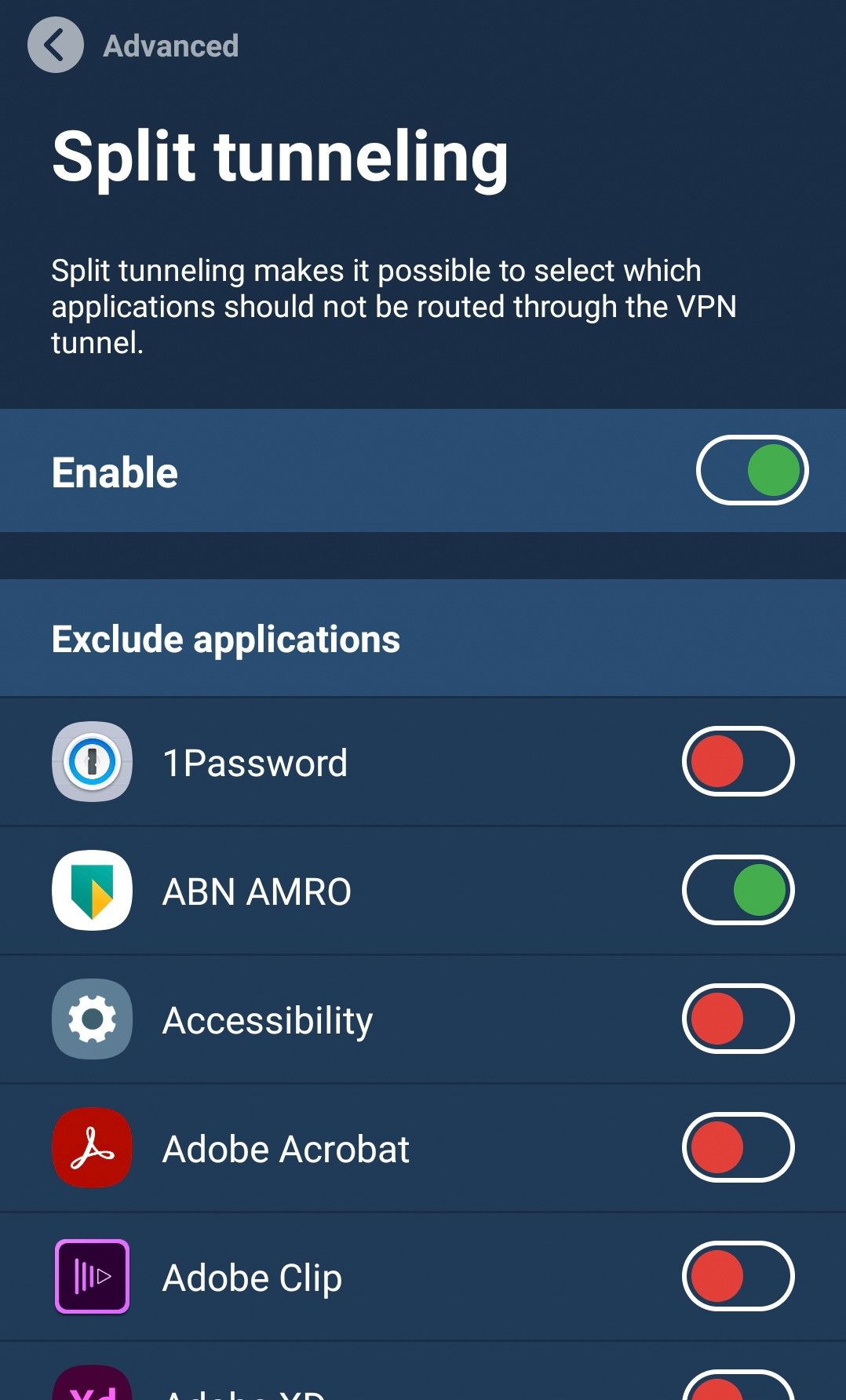
How do I use Mullvad’s split tunneling feature?
The feature is currently available on Windows, Android, and Linux versions of the Mullvad VPN app.
You can find the setting under Settings > Advanced > Split tunneling. Platform-specific details can be found in our split tunneling guide.
Up next
This article is in a five-part series on split tunneling – all written by a Mullvad developer. Stay tuned for the next installment which will discuss split tunneling and traffic leaks.
If you missed the previous articles, we invite you to peruse them at your leisure:
- What is split tunneling?
- When is split tunneling useful?
- The limitations of split tunneling (this article)
- Can split tunneling be leaking traffic?
- Foundations of secure split tunneling
For the universal right to privacy,
Mullvad VPN