OpenWrt routers and Mullvad VPN
Routers OpenVPN Installation Router OpenWrt
Last updated:
Follow this guide to set up a router with OpenWrt and connect to Mullvad VPN.
This guide is using OpenWrt 22.03.2 with an OpenVPN configuration. If you want to use WireGuard instead then see our guide WireGuard on a router.
What this guide covers
What is OpenWrt?
Briefly, "The OpenWrt Project is a Linux operating system targeting embedded devices." Visit the OpenWrt website for more information.
Check OpenWrt's list of supported routers to see if it works with your router.
Benefits to using OpenWrt on your router
Installing OpenWrt and Mullvad on your router comes with some benefits:
- You can secure your whole network and all devices connected to the router.
- You can run Mullvad on more than five devices (all devices connected to the router).
- Via the router, you can even run Mullvad on connected devices that have no support for OpenVPN.
- A router is designed for routing, naturally, and is not disturbed by other programs and settings like a program in a computer might be. It works well and is stable.
Expected performance of OpenVPN on a router
Running OpenVPN on a router is demanding. On a router with a 400mhz ARM CPU, you can expect performance around 7–10Mbps. It scales relatively linearly, so on a router with 1.6Ghz ARM CPU we would expect performance around 30–35 Mbps.
For other speed-related questions, please read our Speed Guide.
Also keep in mind that OpenVPN itself does not use multiple cores and that x86 CPUs will perform a lot better.
Requirements
You will need the following to complete this guide:
- An OpenWrt supported router
- Two Ethernet cables
- A SSH client (for command line use). Linux and Mac have this built-in. For Windows, use PuTTY.
- A valid Mullvad account number.
Set up the router
Connect network cables to the router
- Connect your Internet cable to the Internet port of the intended OpenWrt router.
- Plug the other network cable from your computer to the LAN port.
- Plug in the router and power it on.
Update the router's firmware to OpenWrt
Download the OpenWrt firmware for your specific router from OpenWrt's website, using the Table of Hardware or the Firmware selector. If you use the Table of Hardware then use the "Install URL", not the "Upgrade URL" if this is the first time you install on the router. Don't download using the "snapshot URL" (the snapshot does not include "luci").
Follow your router's instructions on how to connect and update the firmware to the OpenWrt firmware that you downloaded.
The router normally displays some status information and then restarts. Take extra care in downloading the correct version since doing this incorrectly could "brick" your router, making it unusable.
Set a password and enable SSH access
- Open a browser and navigate to http://192.168.1.1/.
- Click the Login button. This logs you in with the default root user and no password.
- Once the Status page loads, you will see a message at the top saying “No password set!”. Click System - Administration.
- On the Router Password page, set a secure password. Click the Save & Apply button at the bottom of the page.
- On the same page, in the SSH Access section, set the interface to LAN. Click the Save & Apply button.
Install necessary software packages
1. Navigate to System - Software and click "Update lists..." after finished updating reload the router page.
2. In download and install package enter the following, one by one, followed by clicking OK and Install. Let the install finish, and then click Dismiss :
- openvpn-openssl
- luci-app-openvpn
- openssl-util
3. Refresh the webpage.
Configure Mullvad on the router
Download an OpenVPN configuration file
- Go to our OpenVPN configuration file generator.
- Use "Android/Chrome OS" as platform, select a location.
- Click on "Advanced settings" and enable "Use IP addresses".
- Click on "Download file" and save the file to your computer.
Add a new VPN connection
- In the menu, select VPN - OpenVPN.
- Under OVPN configuration file upload, set the instance name to "mullvad_client". (Make sure this is correct).
- Click "Choose File".
- Select the downloaded OpenVPN configuration file you previously downloaded.
- Click "Upload".
- Click "Edit" on the mullvad_client line.
- Edit the line
auth-user-passand change it to this
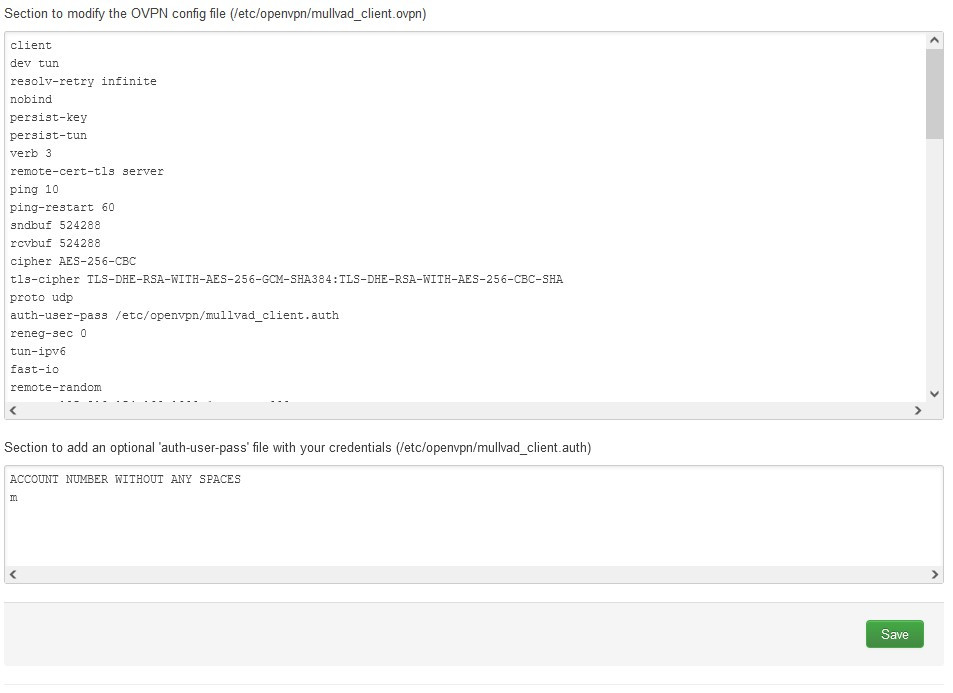
auth-user-pass /etc/openvpn/mullvad_client.auth -
In the box below "Section to add an optional.."
1. Enter your Mullvad account number on a line (without any spaces).
2. Then on a new line enter a single m.
-
Click "Save".
Configure the interface and the firewall
- From the menu at the top, select Network - Interfaces.
- Click “Add new interface” .
-
Name of new interface: enter “MULLVAD_VPN” (this must be entered exactly as shown)
Protocol: Unmanaged
Device: tun0 (Ethernet Adapter)
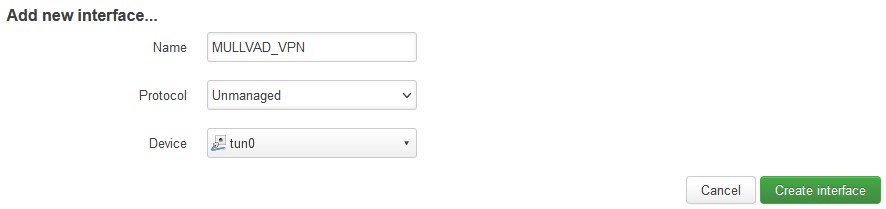
- Click "Create interface" followed by "Save"
- Go to Network - Interfaces - WAN (click "edit") - Advanced Settings - Use DNS servers advertised by peer (disable).
Update the firewall with SSH
Now log in to the router with SSH (using a Linux or MacOS terminal or PuTTY for Windows). Example:
macOS / Linux: ssh -l root 192.168.1.1
Windows: use PuTTY and connect to 192.168.1.1 as root
1. Run the following command:
cat >> /etc/config/firewall << EOF
2. Copy the following text and paste it into the terminal:
config zone
option name 'VPN_FW'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option network 'MULLVAD_VPN'
config forwarding
option dest 'VPN_FW'
option src 'lan'
EOF
3. Hit the Enter key on the keyboard to finish, so the text is added to the file.
Login to your router again from a browser.
From the main menu, navigate to Network - Interfaces - LAN (click "Edit") - DHCP Server - Advanced Settings.
In the “DHCP-Options” field enter the value 6,10.8.0.1.
Click on Save & Apply.
Add a kill switch
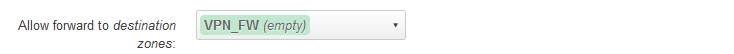
Go to Network > Firewall and click on the Edit button for the "lan" zone.
Under "Allow forward to destination zones": click on the box and uncheck wan.
Restart and verify that it works
Restart your router by going to System - reboot.
Test your IP address
Use our Connection check to see which IP address you are using. It should be one of Mullvad's and not your own.
Make sure that your clients that are using the router as a gateway renew their DHCP lease, so that they get the new DNS pushed to them.
Troubleshooting
DNS leaks
If the router is leaking the DNS servers from your Internet provider then try to change some of the following settings and then restart the router and the computers/devices in the local network that are connected to the router.
- Network > Interfaces > WAN (click edit) > Advanced Settings > Use DNS servers advertised by peer (disable)
- Network > DHCP and DNS > Advanced Settings > Strict order (enable)
- Network > Interfaces > LAN > DHCP Server > Advanced Settings > "Force DHCP on this network even if another server is detected" (enable)
- Network > Interfaces > LAN > DHCP Server > IPv6 Settings > Router Advertisement-Service (disable)